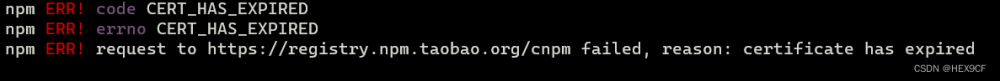
手动更新所有证书,执行命令
kubeadm alpha certs renew all
更新用户配置
kubeadm alpha kubeconfig user --client-name=admin
kubeadm alpha kubeconfig user --org system:masters --client-name kubernetes-admin > /etc/kubernetes/admin.conf
kubeadm alpha kubeconfig user --client-name system:kube-controller-manager > /etc/kubernetes/controller-manager.conf
kubeadm alpha kubeconfig user --org system:nodes --client-name system:node:$(hostname) > /etc/kubernetes/kubelet.conf
kubeadm alpha kubeconfig user --client-name system:kube-scheduler > /etc/kubernetes/scheduler.conf
用更新后的admin.conf替换/root/.kube/config文件文章来源:https://www.toymoban.com/news/detail-762033.html
cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
[root@hadoop101 ~]# kubectl get nodes
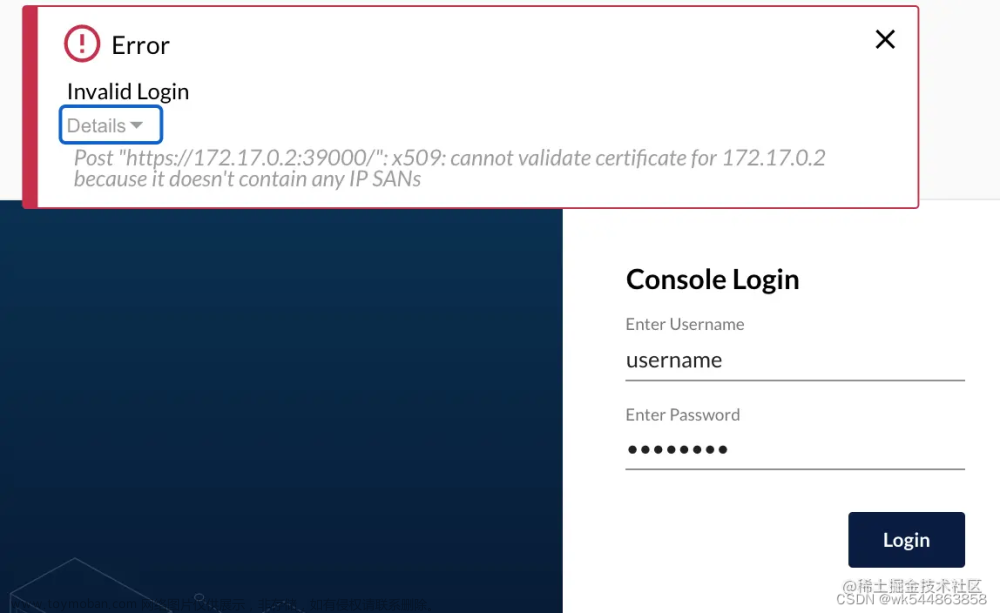
Unable to connect to the server: x509: certificate has expired or is not yet valid
[root@hadoop101 ~]# cd /etc/kubernetes/pki
[root@hadoop101 pki]# openssl x509 -in apiserver.crt -noout -text |grep ' Not '
Not Before: Aug 7 13:30:11 2021 GMT
Not After : Aug 7 13:30:11 2022 GMT
[root@hadoop101 pki]# kubeadm alpha certs check-expiration
[check-expiration] Reading configuration from the cluster...
[check-expiration] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -oyaml'
[check-expiration] Error reading configuration from the Cluster. Falling back to default configuration
W0220 23:39:44.971317 11117 configset.go:202] WARNING: kubeadm cannot validate component configs for API groups [kubelet.config.k8s.io kubeproxy.config.k8s.io]
CERTIFICATE EXPIRES RESIDUAL TIME CERTIFICATE AUTHORITY EXTERNALLY MANAGED
admin.conf Aug 07, 2022 13:30 UTC <invalid> no
apiserver Aug 07, 2022 13:30 UTC <invalid> ca no
apiserver-etcd-client Aug 07, 2022 13:30 UTC <invalid> etcd-ca no
apiserver-kubelet-client Aug 07, 2022 13:30 UTC <invalid> ca no
controller-manager.conf Aug 07, 2022 13:30 UTC <invalid> no
etcd-healthcheck-client Aug 07, 2022 13:30 UTC <invalid> etcd-ca no
etcd-peer Aug 07, 2022 13:30 UTC <invalid> etcd-ca no
etcd-server Aug 07, 2022 13:30 UTC <invalid> etcd-ca no
front-proxy-client Aug 07, 2022 13:30 UTC <invalid> front-proxy-ca no
scheduler.conf Aug 07, 2022 13:30 UTC <invalid> no
CERTIFICATE AUTHORITY EXPIRES RESIDUAL TIME EXTERNALLY MANAGED
ca Aug 05, 2031 13:30 UTC 8y no
etcd-ca Aug 05, 2031 13:30 UTC 8y no
front-proxy-ca Aug 05, 2031 13:30 UTC 8y no
[root@hadoop101 pki]# kubeadm alpha certs renew all
[renew] Reading configuration from the cluster...
[renew] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -oyaml'
[renew] Error reading configuration from the Cluster. Falling back to default configuration
W0220 23:41:15.686121 11419 configset.go:202] WARNING: kubeadm cannot validate component configs for API groups [kubelet.config.k8s.io kubeproxy.config.k8s.io]
certificate embedded in the kubeconfig file for the admin to use and for kubeadm itself renewed
certificate for serving the Kubernetes API renewed
certificate the apiserver uses to access etcd renewed
certificate for the API server to connect to kubelet renewed
certificate embedded in the kubeconfig file for the controller manager to use renewed
certificate for liveness probes to healthcheck etcd renewed
certificate for etcd nodes to communicate with each other renewed
certificate for serving etcd renewed
certificate for the front proxy client renewed
certificate embedded in the kubeconfig file for the scheduler manager to use renewed
[root@hadoop101 pki]# ll
总用量 56
-rw-r--r-- 1 root root 1220 2月 20 23:41 apiserver.crt
-rw-r--r-- 1 root root 1090 2月 20 23:41 apiserver-etcd-client.crt
-rw------- 1 root root 1675 2月 20 23:41 apiserver-etcd-client.key
-rw------- 1 root root 1679 2月 20 23:41 apiserver.key
-rw-r--r-- 1 root root 1099 2月 20 23:41 apiserver-kubelet-client.crt
-rw------- 1 root root 1675 2月 20 23:41 apiserver-kubelet-client.key
-rw-r--r-- 1 root root 1025 8月 7 2021 ca.crt
-rw------- 1 root root 1679 8月 7 2021 ca.key
drwxr-xr-x 2 root root 162 8月 7 2021 etcd
-rw-r--r-- 1 root root 1038 8月 7 2021 front-proxy-ca.crt
-rw------- 1 root root 1675 8月 7 2021 front-proxy-ca.key
-rw-r--r-- 1 root root 1058 2月 20 23:41 front-proxy-client.crt
-rw------- 1 root root 1679 2月 20 23:41 front-proxy-client.key
-rw------- 1 root root 1679 8月 7 2021 sa.key
-rw------- 1 root root 451 8月 7 2021 sa.pub
[root@hadoop101 pki]# openssl x509 -in apiserver.crt -noout -text |grep ' Not '
Not Before: Aug 7 13:30:11 2021 GMT
Not After : Feb 20 15:41:16 2024 GMT
[root@hadoop101 pki]# cd /etc/kubernetes
[root@hadoop101 kubernetes]# kubeadm alpha kubeconfig user --client-name=admin
I0220 23:44:51.209752 12126 version.go:252] remote version is much newer: v1.26.1; falling back to: stable-1.18
W0220 23:44:52.663332 12126 configset.go:202] WARNING: kubeadm cannot validate component configs for API groups [kubelet.config.k8s.io kubeproxy.config.k8s.io]
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN5RENDQWJDZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJeE1EZ3dOekV6TXpBeE1Wb1hEVE14TURnd05URXpNekF4TVZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTmo4CkgrZW5lSEdWek9KTUJyK3dhQkxoOVhtTXVqSFpXcmVWT0ZxT0EvMENPdnllSEJ4dkJqNGM4SjRNeEJQd0R1NmQKMmEydXdKbHZpUm1ndWJIMllyT3VvY1hMem5jUUV4S2tzeG5KdzhocHVpMVAxK2tYd2hpaWFlRjhib25iTnFMWgovZ0RVQnB6aUI4ZkxGSE1lTXBmS3lYc0pWMjcxNG4xUnhVb1VobFlJaHpaNWZ2TlFYZUVXRkZxM1k2Rm5IUEFBClVoNUxhakNzc21NSVpuL0E4UUU5QlpqYTFXeEhlcHNGeEJoUTRiUFhnWXRWa0UwbEF0MzFnNVV4blhHSEU3OCsKazFNc3lvK0dOdVJRS2JUZHRkQ0Q2UzFwOWhnQ0JFSmdSeTFWOFV6ZkhabXZFVCttMk9WME9EY2w0SkxHWng4RApwbVZMa2J0bldhQ1lYOElxcVRjQ0F3RUFBYU1qTUNFd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFHdnB5cjNTQzRCRy9wTDA3b0pNMFFKWTkrZHIKWHhkYkROWS9oQmRzRXpiZWRkQnptZ0hnekF1eUN1UDE1SmZRSVA3YmxUZjdMTGF5Qk9EOHRPQ3dXdGhvM1VZNgpMSjN3TnRzTmE2MEFlaDd6aVVFaEVWdWJLekJFOEZLTUNMeitOZzk2YSsxRUhjeWZjU2YybTVaeFFUNWxaRk90CllpMjUzdFQzckpVMFdWcmtCeE1KOXY5YkxlMkpKWFVtLzdzSWJCWmVpdExXTEhNdkhYMDZMUWkwbHhxWGVhU3YKY0tLaEJCeGN1Q3poRk4wKzFxODVFcVJkS2JvTVQ1K1hRV0s1TGVORHd2K1luQ1k5Z0FHS0NCM2JwZ3JaTXdEdgozTFJTMC9ZeC8yWFdOZDZUNklYSlk5SWhYTitrK3ozYzhpbVFzTWtHWVVwWDVFbnNtQk5CUUplaGkwTT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
server: https://192.168.10.101:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: admin
name: admin@kubernetes
current-context: admin@kubernetes
kind: Config
preferences: {}
users:
- name: admin
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN6akNDQWJhZ0F3SUJBZ0lJWTJnV2ZpTEpBbmN3RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TVRBNE1EY3hNek13TVRGYUZ3MHlOREF5TWpBeE5UUTBOVE5hTUJBeApEakFNQmdOVkJBTVRCV0ZrYldsdU1JSUJJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBCnM3enpDb2oyZndGUEJQeVFtZHVoYjJ6Z1M5VktUdjhyVDM0eDhGYmhjREQ4cDJKUjdKWUhaSXU4Z0MrS09xa2EKcXRLTUZlUnRoN3UrQnFTUWdqQVBrdm5lREJ3Z2lyWnQ0Vnp5WFpZWUdHS3dQMVNpVnB1KzBERUpQMVNhYzhIVApWdDk0eHhjc09zTC95alYyZjRIY1R1NlpjNDB6Q1VETm1hR3ZpNzYxV0hUdEpzOE1iN01QVU9lNkdqN2dXR0xVCjRpcVlPbm1Pa2IzeUJuVUxIbjZKZVV2RVVJZERMMFZsOVYxc0RQLys0dmc3U0lKMEtjNE5MT01YQWprMzVUTVIKYmhVeW04SzdDK1p1cnNUUjlpbnNTejMzT1B6YVVnYzFSSGl3SFpFc3V1UWQweGh3clR0OW9sdFgveXNrYUplMwpkVW1jeTN3a0RUU2N5b2o3MmdndFRRSURBUUFCb3ljd0pUQU9CZ05WSFE4QkFmOEVCQU1DQmFBd0V3WURWUjBsCkJBd3dDZ1lJS3dZQkJRVUhBd0l3RFFZSktvWklodmNOQVFFTEJRQURnZ0VCQUNiMUtwbHBxT2w4VHhzaUVwZHMKaEFxWms1TTlRV1hiZUxvWGkxMm1kNVQ1ZVRxR2FYa1ltYWVHM3k5WFN4UGhUSy9WdUx1NlNtUmc1THJPbThsYgpIL3AyOGw0bDA4SzRWTjAxTWI4TlM2OXlWcXN0KzIrakgzZEpuSkYxSlEwNlBMQjdpdjVVQXJGRVlmdGlhVFJtCnJxVFpoNndyUVBMd1dnWEQya3NzaXVreEdGTitOS3pqMGRtOTloZUtsdzhzdjVhWXVJNlpCR1NCYkY1cmJ3MW8KeU01R3laMDJPVWVzSEFXSUxHN2NGZnRMb1Y1R1NRMUt4YTV3VCtBa0RJbVAzOFFwSDhGdG45dEJ2TWFyb3RyNgozSTFhaFd4a3o0UGhuaTJVMGIvM2plTWJENnlIaVIwVmkyRFEzbnRCN2ovM2hHdUYycnJYaG45dXdoOWJ3QTFNCnhOcz0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcEFJQkFBS0NBUUVBczd6ekNvajJmd0ZQQlB5UW1kdWhiMnpnUzlWS1R2OHJUMzR4OEZiaGNERDhwMkpSCjdKWUhaSXU4Z0MrS09xa2FxdEtNRmVSdGg3dStCcVNRZ2pBUGt2bmVEQndnaXJadDRWenlYWllZR0dLd1AxU2kKVnB1KzBERUpQMVNhYzhIVFZ0OTR4eGNzT3NML3lqVjJmNEhjVHU2WmM0MHpDVURObWFHdmk3NjFXSFR0SnM4TQpiN01QVU9lNkdqN2dXR0xVNGlxWU9ubU9rYjN5Qm5VTEhuNkplVXZFVUlkREwwVmw5VjFzRFAvKzR2ZzdTSUowCktjNE5MT01YQWprMzVUTVJiaFV5bThLN0MrWnVyc1RSOWluc1N6MzNPUHphVWdjMVJIaXdIWkVzdXVRZDB4aHcKclR0OW9sdFgveXNrYUplM2RVbWN5M3drRFRTY3lvajcyZ2d0VFFJREFRQUJBb0lCQVFDVDJidzdVRXNrVWxsRQpDdGFRR2NFRVBaV01DOW5pZmJpTTNZd0szZ3o0RXZQaVpOaHJPMGE5aU16NHpTSngrcVQ3RzlNc053bDZmQTltCnUzdzcrM2owT0NKVjU5VkZCYWdCbUVtdWZrYzMyQWFQTWZtUU1QR1hwSjZzdjlXRm4wMVB5dWc1TFhDdXJiVm8KQ3U1OUdMKzNGa0tZY1BBb2ptd1NFcFNxNmFlWEtNYjFKTDlKL1BlQTQzdlZnQXVlbm5aRFdGWG14OWVoZERxZAp0N21PdVMxRTNEWUZLaitZaTEvWGpQRVBteGRCSmFXWW16YStoN1czd0lUblJFbW1Ob0FlR3F2aFB2Q3RKb2hzCkEvK24vMWY3cEs2RG04cWgyYnFNNEhUdmR0K2hsVmVnMHV4Wi9oRjZMV3JPam41eFlaWU5PV05oY0pveG9LdTgKazZaRlFFckJBb0dCQU5rcUxidlVzRk1tbDJVYzZLRUVGUkNWbzlRWTVhT2pnK05WQ1cxWEF4V2Y0Q2xtb2Y3UAo1REl6aXNEYVJjUXZ1bmQ1RWdXKzl3MlcvVzcweWNOOWY4a1pJTnJiTDd6cFJYS24zM01ocFdBVytrL1RjT3lECjZXek9oaFRhY1ppblNhQnhKKzJCOTZCVEFnRFluRUtJT25lQTE3VytjVmNVWWVhL1l2V0NjTHRKQW9HQkFOUGgKWDg5VEd2Y1BEVVNlL2I4Q0RCUkcxYTdRVzZkWGNFdlQxa1pKc2tWalpsUjNMNCtZMVhUNGc2T0RJWWNIWnZPQgpMWEM4WkI0a0ZJZzFnaVFjeU9wMUl4a2VMUUJnVHVIYjkxVFd5R3BoS2hZZGJDMmpaVTR1RTZZRjVTVlJHQXhIClA5dFk0UEZxSXZ1UEJib1h3SjkwdWs2aVdYZjRUbDU5elpBVHpuM2xBb0dCQUw4ZmZleUhQVCtSQVVEOTlrWnYKWDFLZlAvWVVpMVkvUEgzQWczRjFXTU9aVnlGWXNFMmdEVWVaVVE1MWkxMGtYRWwxaGtVRVVrM2xpdG95R2JneApKVnVJLy85ZFZHQkFOTnk1bmRDbjFmSUJodjdtS2NZZU9qdUdiejYvR2FhdDVBQ09WZ09UbEtuSEpFWTJYUis0CjRTdjNldUQ2NEtrd3lSRFpjM0I3QWxmeEFvR0FKNkJ5QzlOdUtxQzlDWVYyelo5elpPTnVtWGhNZS9xbGZQa00KalM3QlVhcnFlNGVpOUlkUC9NVngwVVg0SWtubkhrbWRsd1VVOEhJdENPQ0JDNEg2cmFia3ZwRGZONy9MWVFDRAp2SEZESUdvMXRkY2c0VlE2NFNsSzhYVU95ekRrZjM5ZjJRVkJaTVZGNzZockdNZlNkY0FlREJEZkRNbjYxajlQCkQ5QTBnV1VDZ1lCVGdicGFmVkpwWVA5UVU2YjdzV0Jpc3A1UDJZOHBJOGlNWW53ZUI4eGcvT2dlU0lEWk4yNUgKS2hKUW5IU0tMdFBWWGtPVXgrbG9LWnpudTBxZjhpMUhnU3dIdGpiZjNib1FhNGdmcFJOWVZFQlYzTGJ1eldTdApKVU5UR0FBRE9OV0lyMDN5RDZCMlNCMk9FUFpxYUNqUzVPZTZzV0RXalJvQ2Z0NmtGeU9nK2c9PQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=
[root@hadoop101 kubernetes]# kubeadm alpha kubeconfig user --org system:masters --client-name kubernetes-admin > /etc/kubernetes/admin.conf
I0220 23:44:56.000673 12148 version.go:252] remote version is much newer: v1.26.1; falling back to: stable-1.18
W0220 23:44:57.284954 12148 configset.go:202] WARNING: kubeadm cannot validate component configs for API groups [kubelet.config.k8s.io kubeproxy.config.k8s.io]
[root@hadoop101 kubernetes]# kubeadm alpha kubeconfig user --client-name system:kube-controller-manager > /etc/kubernetes/controller-manager.conf
I0220 23:44:58.420659 12164 version.go:252] remote version is much newer: v1.26.1; falling back to: stable-1.18
W0220 23:44:59.647838 12164 configset.go:202] WARNING: kubeadm cannot validate component configs for API groups [kubelet.config.k8s.io kubeproxy.config.k8s.io]
[root@hadoop101 kubernetes]# kubeadm alpha kubeconfig user --org system:nodes --client-name system:node:$(hostname) > /etc/kubernetes/kubelet.conf
I0220 23:45:00.850679 12187 version.go:252] remote version is much newer: v1.26.1; falling back to: stable-1.18
W0220 23:45:02.317471 12187 configset.go:202] WARNING: kubeadm cannot validate component configs for API groups [kubelet.config.k8s.io kubeproxy.config.k8s.io]
[root@hadoop101 kubernetes]# kubeadm alpha kubeconfig user --client-name system:kube-scheduler > /etc/kubernetes/scheduler.conf
I0220 23:45:06.973889 12208 version.go:252] remote version is much newer: v1.26.1; falling back to: stable-1.18
W0220 23:45:07.855108 12208 configset.go:202] WARNING: kubeadm cannot validate component configs for API groups [kubelet.config.k8s.io kubeproxy.config.k8s.io]
[root@hadoop101 kubernetes]# cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
cp:是否覆盖"/root/.kube/config"? y
[root@hadoop101 kubernetes]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
hadoop101 Ready master 562d v1.18.0
hadoop102 Ready <none> 562d v1.18.0
hadoop103 Ready <none> 562d v1.18.0
[root@hadoop101 kubernetes]# systemctl restart kube-apiserver
Failed to restart kube-apiserver.service: Unit not found.
[root@hadoop101 kubernetes]# systemctl restart kube-apiserver
Failed to restart kube-apiserver.service: Unit not found.
[root@hadoop101 kubernetes]# kubectl -n david-test get po -o wide
No resources found in david-test namespace.
[root@hadoop101 kubernetes]# kubectl get pod -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-f89759699-qnfxv 1/1 Running 0 562d 10.244.2.3 hadoop103 <none> <none>
[root@hadoop101 kubernetes]# kubectl get modes
error: the server doesn't have a resource type "modes"
[root@hadoop101 kubernetes]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
hadoop101 Ready master 562d v1.18.0
hadoop102 Ready <none> 562d v1.18.0
hadoop103 Ready <none> 562d v1.18.0
[root@hadoop101 kubernetes]# kubectl get po -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-f89759699-qnfxv 1/1 Running 0 562d 10.244.2.3 hadoop103 <none> <none>
[root@hadoop101 kubernetes]#
k8s解决证书过期官方文档:https://kubernetes.io/zh-cn/docs/tasks/administer-cluster/kubeadm/kubeadm-certs/
帮助文档: https://www.cnblogs.com/00986014w/p/13095628.html文章来源地址https://www.toymoban.com/news/detail-762033.html
到了这里,关于Unable to connect to the server: x509: certificate has expired or is not yet valid的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!